- A+
简介:
IPsec VPN全称(Internet Protocol Security Virtual Private Network)IP安全协议虚拟专用网。它是指采用IPsec协议来实现的一种VPN技术。是由Internet Engineering Task Force (IETF) 定义的安全标准框架,在公网上为两个私有网络提供安全通信通道,通过包封装对通道加密,保证连接的安全——在两个公共网关间提供私密数据封包服务。
环境准备
- 服务器系统:Ubuntu 16.04
- 香港VPS一台
一、服务器端安装
项目地址:https://github.com/hwdsl2/setup-ipsec-vpn
下载脚本
wget https://git.io/vpnquickstart -O vpn.sh && sudo sh vpn.sh
脚本内容如下:
#!/bin/sh
#
# Quick start script to set up an IPsec VPN server on Ubuntu, Debian,
# CentOS/RHEL, Rocky Linux, AlmaLinux, Amazon Linux 2 and Alpine Linux
# Works on any dedicated server or virtual private server (VPS)
#
# DO NOT RUN THIS SCRIPT ON YOUR PC OR MAC!
#
# The latest version of this script is available at:
# https://github.com/hwdsl2/setup-ipsec-vpn
#
# Copyright (C) 2021 Lin Song <linsongui@gmail.com>
#
# This work is licensed under the Creative Commons Attribution-ShareAlike 3.0
# Unported License: http://creativecommons.org/licenses/by-sa/3.0/
#
# Attribution required: please include my name in any derivative and let me
# know how you have improved it!
export PATH="/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin"
exiterr() { echo "Error: $1" >&2; exit 1; }
check_root() {
if [ "$(id -u)" != 0 ]; then
exiterr "Script must be run as root. Try 'sudo sh $0'"
fi
}
check_vz() {
if [ -f /proc/user_beancounters ]; then
exiterr "OpenVZ VPS is not supported."
fi
}
check_lxc() {
# shellcheck disable=SC2154
if [ "$container" = "lxc" ] && [ ! -e /dev/ppp ]; then
cat 1>&2 <<'EOF'
Error: /dev/ppp is missing. LXC containers require configuration.
See: https://github.com/hwdsl2/setup-ipsec-vpn/issues/1014
EOF
exit 1
fi
}
check_os() {
os_type=centos
rh_file="/etc/redhat-release"
if grep -qs "Red Hat" "$rh_file"; then
os_type=rhel
fi
if grep -qs "release 7" "$rh_file"; then
os_ver=7
elif grep -qs "release 8" "$rh_file"; then
os_ver=8
grep -qi stream "$rh_file" && os_ver=8s
grep -qi rocky "$rh_file" && os_type=rocky
grep -qi alma "$rh_file" && os_type=alma
elif grep -qs "Amazon Linux release 2" /etc/system-release; then
os_type=amzn
os_ver=2
else
os_type=$(lsb_release -si 2>/dev/null)
[ -z "$os_type" ] && [ -f /etc/os-release ] && os_type=$(. /etc/os-release && printf '%s' "$ID")
case $os_type in
[Uu]buntu)
os_type=ubuntu
;;
[Dd]ebian)
os_type=debian
;;
[Rr]aspbian)
os_type=raspbian
;;
[Aa]lpine)
os_type=alpine
;;
*)
cat 1>&2 <<'EOF'
Error: This script only supports one of the following OS:
Ubuntu, Debian, CentOS/RHEL 7/8, Rocky Linux, AlmaLinux,
Amazon Linux 2 or Alpine Linux
EOF
exit 1
;;
esac
if [ "$os_type" = "alpine" ]; then
os_ver=$(. /etc/os-release && printf '%s' "$VERSION_ID" | cut -d '.' -f 1,2)
if [ "$os_ver" != "3.14" ]; then
exiterr "This script only supports Alpine Linux 3.14."
fi
else
os_ver=$(sed 's/..*//' /etc/debian_version | tr -dc 'A-Za-z0-9')
if [ "$os_ver" = "8" ] || [ "$os_ver" = "jessiesid" ]; then
exiterr "Debian 8 or Ubuntu < 16.04 is not supported."
fi
fi
fi
}
check_iface() {
def_iface=$(route 2>/dev/null | grep -m 1 '^default' | grep -o '[^ ]*$')
if [ "$os_type" != "alpine" ]; then
[ -z "$def_iface" ] && def_iface=$(ip -4 route list 0/0 2>/dev/null | grep -m 1 -Po '(?<=dev )(S+)')
fi
def_state=$(cat "/sys/class/net/$def_iface/operstate" 2>/dev/null)
check_wl=0
if [ -n "$def_state" ] && [ "$def_state" != "down" ]; then
if [ "$os_type" = "ubuntu" ] || [ "$os_type" = "debian" ] || [ "$os_type" = "raspbian" ]; then
if ! uname -m | grep -qi -e '^arm' -e '^aarch64'; then
check_wl=1
fi
else
check_wl=1
fi
fi
if [ "$check_wl" = "1" ]; then
case $def_iface in
wl*)
exiterr "Wireless interface '$def_iface' detected. DO NOT run this script on your PC or Mac!"
;;
esac
fi
}
check_iptables() {
if [ "$os_type" = "ubuntu" ] || [ "$os_type" = "debian" ] || [ "$os_type" = "raspbian" ]; then
if [ -x /sbin/iptables ] && ! iptables -nL INPUT >/dev/null 2>&1; then
exiterr "IPTables check failed. Reboot and re-run this script."
fi
fi
}
wait_for_apt() {
count=0
apt_lk=/var/lib/apt/lists/lock
pkg_lk=/var/lib/dpkg/lock
while fuser "$apt_lk" "$pkg_lk" >/dev/null 2>&1
|| lsof "$apt_lk" >/dev/null 2>&1 || lsof "$pkg_lk" >/dev/null 2>&1; do
[ "$count" = "0" ] && echo "## Waiting for apt to be available..."
[ "$count" -ge "100" ] && exiterr "Could not get apt/dpkg lock."
count=$((count+1))
printf '%s' '.'
sleep 3
done
}
install_pkgs() {
if ! command -v wget >/dev/null 2>&1; then
if [ "$os_type" = "ubuntu" ] || [ "$os_type" = "debian" ] || [ "$os_type" = "raspbian" ]; then
wait_for_apt
export DEBIAN_FRONTEND=noninteractive
(
set -x
apt-get -yqq update
) || exiterr "'apt-get update' failed."
(
set -x
apt-get -yqq install wget >/dev/null
) || exiterr "'apt-get install wget' failed."
elif [ "$os_type" != "alpine" ]; then
(
set -x
yum -y -q install wget >/dev/null
) || exiterr "'yum install wget' failed."
fi
fi
if [ "$os_type" = "alpine" ]; then
(
set -x
apk add -U -q bash coreutils grep net-tools sed wget
) || exiterr "'apk add' failed."
fi
}
get_setup_url() {
base_url="https://github.com/hwdsl2/setup-ipsec-vpn/raw/master"
sh_file="vpnsetup_ubuntu.sh"
if [ "$os_type" = "centos" ] || [ "$os_type" = "rhel" ] || [ "$os_type" = "rocky" ] || [ "$os_type" = "alma" ]; then
sh_file="vpnsetup_centos.sh"
elif [ "$os_type" = "amzn" ]; then
sh_file="vpnsetup_amzn.sh"
elif [ "$os_type" = "alpine" ]; then
sh_file="vpnsetup_alpine.sh"
fi
setup_url="$base_url/$sh_file"
}
run_setup() {
status=0
if tmpdir=$(mktemp --tmpdir -d vpn.XXXXX 2>/dev/null); then
if ( set -x; wget -t 3 -T 30 -q -O "$tmpdir/vpn.sh" "$setup_url"
|| curl -fsL "$setup_url" -o "$tmpdir/vpn.sh" 2>/dev/null ); then
if /bin/bash "$tmpdir/vpn.sh"; then
if [ -s /opt/src/ikev2.sh ] && [ ! -f /etc/ipsec.d/ikev2.conf ]; then
sleep 1
/bin/bash /opt/src/ikev2.sh --auto || status=1
fi
else
status=1
fi
else
status=1
echo "Error: Could not download VPN setup script." >&2
fi
/bin/rm -f "$tmpdir/vpn.sh"
/bin/rmdir "$tmpdir"
else
exiterr "Could not create temporary directory."
fi
}
quickstart() {
check_root
check_vz
check_lxc
check_os
check_iface
check_iptables
install_pkgs
get_setup_url
run_setup
}
## Defer setup until we have the complete script
quickstart "$@"
exit "$status"
下载完成后赋权执行脚本
chmod +x vpn.sh sh vpn.sh
执行完成后会有显示相应的IPsec PSK秘钥。还有对应的VPN用户名和密码。
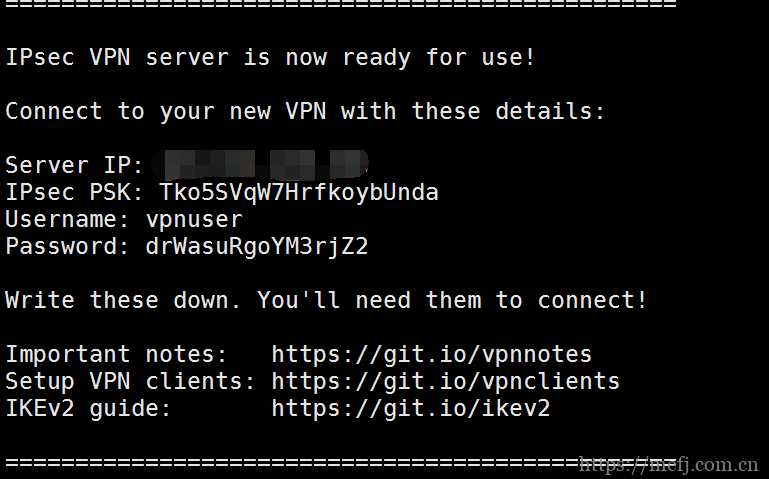
二、客户端安装设置
以安卓端设置为例
- 将生成的
.sswan文件安全地传输到您的 Android 设备。 - 从Google Play、F-Droid或strongSwan 下载服务器安装 strongSwan VPN 客户端。
- 启动 strongSwan VPN 客户端。
- 点击右上角的“更多选项”菜单,然后点击导入 VPN 配置文件。
- 选择
.sswan您从 VPN 服务器传输的文件。
注意:要查找.sswan文件,请点击三行菜单按钮,然后浏览到您保存文件的位置。 - 在“导入 VPN 配置文件”屏幕上,点击从VPN 配置文件导入证书,然后按照提示操作。
- 在“选择证书”屏幕上,选择新的客户端证书,然后点击选择。
- 点击导入。
- 点击新的 VPN 配置文件进行连接。
(可选功能)您可以选择在 Android 上启用“Always-on VPN”功能。启动设置应用程序,转到网络和互联网 -> 高级 -> VPN,单击“strongSwan VPN 客户端”右侧的齿轮图标,然后启用永远在线的 VPN和阻止没有 VPN 的连接选项。如果您在不使用帮助程序脚本的情况下手动设置 IKEv2,请单击此处获取说明。
成功连接后,您可以通过在 Google 上查找您的 IP 地址来验证您的流量是否被正确路由。它应该说“您的公共 IP 地址是Your VPN Server IP”。
如果您在尝试连接时遇到错误,请参阅故障排除。
更多设置和使用,请点击此处查看
- 微信公众号
- 扫一扫关注微信公众号
-

- 运维交流群
- 扫一扫二维码加入群聊
-