- A+
所属分类:Linux
环境
- ASA5550防火墙一台
- 交换机两台
- SDWAN设备一台
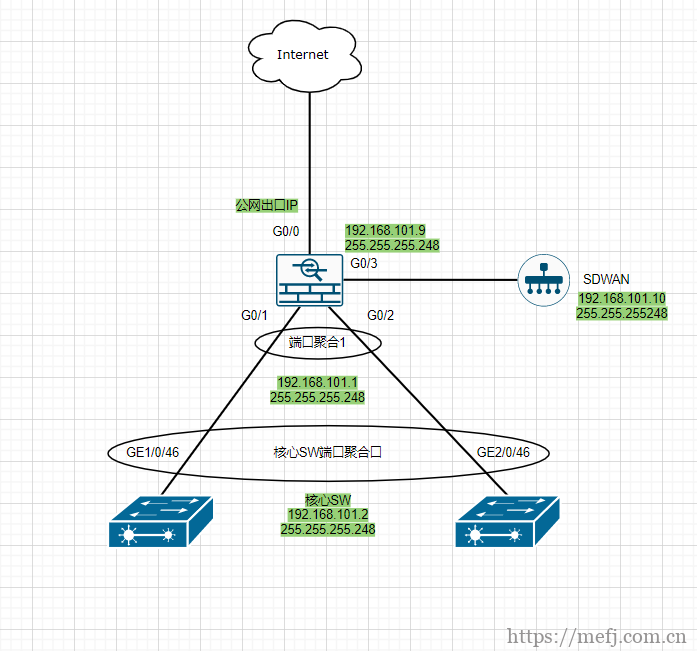
网段划分
- 公网 10.10.10.180 掩码24 网关10.10.10.1
- 内网 192.168.101.0/29
- 管理 10.201.100.1 掩码 24
- SDWAN互联地址192.168.101.0/29
拓扑图
1、ASA基本配置。
conf t hostname FW-5550 clock timezone UTC/GMT -7 interface GigabitEthernet0/0 nameif outside #outside为外网接口名称 security-level 0 #安全等级为0,等级越高权限越大,高等级可以访问低等级。反之低等级不能访问高等级 ip address 10.10.10.180 255.255.255.0 #配置防火墙公网地址 no sh #启用接口 interface port-channel 1 #ASA端新建聚合口port-channel 1 nameif inside #inside为内网接口名称 security-level 100 #安全等级100 为最高,一般用作内网权限等级 ip address 192.168.101.1 255.255.255.248 #配置防火墙到交换机互联地址 no sh #启用接口 interface GigabitEthernet0/1 channel-group 1 mode on #将G0/1端口加到聚合组1 no nameif no security-level no ip address no sh #启用G0/1接口 interface GigabitEthernet0/2 channel-group 1 mode on #将G0/2端口加到聚合组1 no nameif no security-level no ip address no sh #启用G0/2接口 interface GigabitEthernet0/3 no nameif security-level 100 ip address 192.168.101.9 255.255.255.248 no sh interface Management0/0 #进入管理口 nameif management #设置nameif名称为management管理口 security-level 100 ip address 10.201.100.1 255.255.255.0 no sh object network inside #object network 新建内网地址池inside subnet 192.168.101.0 255.255.255.248 #设置内网子网 nat (inside,outside) dynamic interface #单个公网nat转换默认用interface出口进行PAT object network sdwan #object network 新建SDWAN地址池sdwan subnet 192.168.101.8 255.255.255.248 #sdwan互联子网 nat (sdwan,outside) dynamic interface #单个公网nat转换默认用interface出口进行PAT object network sslvpn #object network 新建sslvpn地址池sslvpn subnet 192.168.39.0 255.255.255.0 #sslvpn地址池子网 nat (outside,outside) dynamic interface #单个公网nat转换默认用interface出口进行PAT nat (inside,outside) source static any any destination static sslvpn sslvpn #静态nat转换sslvpn route outside 0.0.0.0 0.0.0.0 10.10.10.1 1 #添加默认路由出网关 route inside 192.168.101.27 255.255.255.0 192.168.101.2 1 #添加下联交换机内网回程路由 route inside 192.168.101.28 255.255.255.0 192.168.101.2 1 #添加下联交换机内网回程路由 route inside 192.168.101.29 255.255.255.0 192.168.101.2 1 #添加下联交换机内网回程路由 domain-name Cisco.com #设置域名 enable password cisco #开启密码登录 username cisco password cisco privilege 15 #新建用户cisco密码cisco aaa authentication enable console LOCAL aaa authentication ssh console LOCAL aaa authentication telnet console LOCAL aaa authentication http console LOCAL asdm image disk0:/asdm-7161.bin #开启ASDM图形管理服务,asdm要上传到ASA flash中 http server enable #开启ASDM http服务 http 0.0.0.0 0.0.0.0 outside http 0.0.0.0 0.0.0.0 inside http 0.0.0.0 0.0.0.0 management telnet 0.0.0.0 0.0.0.0 outside telnet 0.0.0.0 0.0.0.0 inside telnet 0.0.0.0 0.0.0.0 management ssh 0.0.0.0 0.0.0.0 outside ssh 0.0.0.0 0.0.0.0 inside ssh 0.0.0.0 0.0.0.0 management crypto key generate rsa ip local pool ssl-user 192.168.39.1-192.168.39.254 mask 255.255.255.0 #新建sslvpn地址池ssl-user地址池 webvpn enable outside enable inside anyconnect image disk0:/anyconnect-win-4.10.04065-webdeploy-k9.pkg 1 anyconnect enable tunnel-group-list enable group-policy mysslvpn-group internal group-policy mysslvpn-group attributes #新建sslvpn策略组mysslvpn-group split-tunnel-policy tunnelall #分割所有隧道策略 vpn-tunnel-protocol ssl-client ssl-clientless #允许vpn协议厚客户端和无客户端连接 address-pools value ssl-user #允许协议地址池ssl-user dns-server value 8.8.8.8 1.1.1.1 #设置sslvpn地址池的DNS username ssluser password cisco #新建sslvpn用户和密码 username ssluser attributes service-type remote-access #允许远程访问 vpn-group-policy mysslvpn-group #允许mysslvpn-group vpn组策略 copy running-config strat-config #保存配置 可选项 //瘦客户端---端口转发 webvpn port-forward desktop 2030 33.33.33.2 3389 exit group-policy desktop attributes webvpn port-forward enable desktop exit username ssluser attributes vpn-group-policy desktop
SSLVPN相关资源已打包到网盘,关注公众号回复“sslvpn”即可获取下载链接。
https://www.petenetlive.com/KB/Article/0000422
https://sysin.org/blog/cisco-anyconnect-4/
https://www.doc88.com/p-3327119952084.html
https://ishare.iask.sina.com.cn/f/buT1VEWxQVT.html
- 微信公众号
- 扫一扫关注微信公众号
-

- 运维交流群
- 扫一扫二维码加入群聊
-